


AI-powered cyber risk prediction to assess threat, test defences & optimise insurance outcomes.
Pinpoints threats, justifies spend/coverage, quantifies risk, and optimizes defenses to bolster security posture.
Quantifies financial cyber risk & optimizes insurance. Targets security spend and transfers risk to protect capital and shareholder value.



AI-Driven probabilistic risk engine
Citadel’s AI-powered probabilistic engine analyses threat pathways to forecast attack probability and financial exposure, evaluating control efficacy and mitigation strategies to deliver actuarially sound cyber insurance insights.
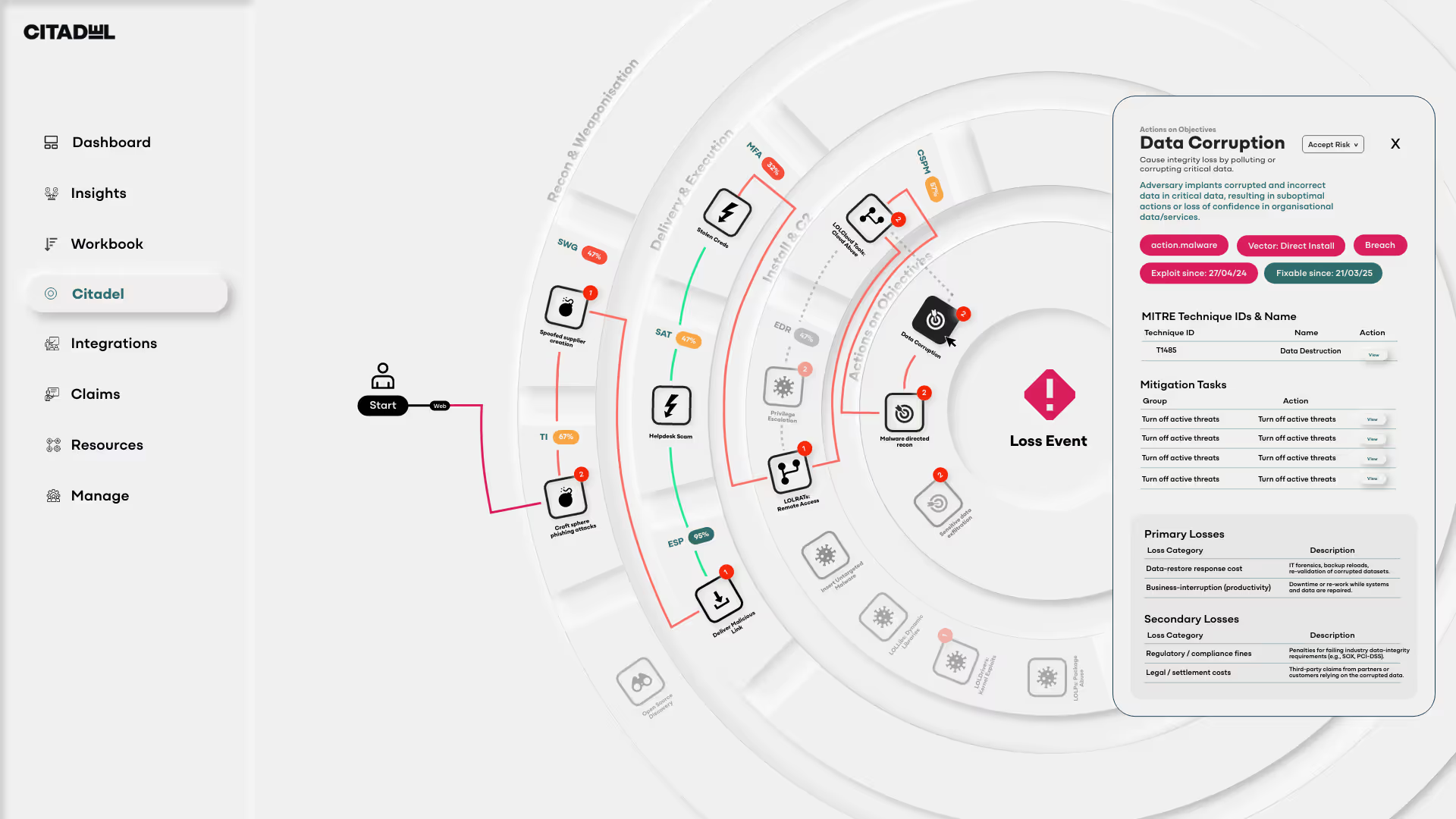
Concentric Rings
Concentric Rings represent attack stages, beginning with Recon and moving inward through stages (Weaponization, Delivery, Exploitation, Installation, Command & Control (C2), and Actions on Objectives), ending with Impact - the point where an insurable loss occurs.
Theat Events
Nodes depict Threat Events—specific instances where a threat actor exploits a vulnerability, risking harm to an information system.
Loss Event Controls
Loss Event Controls are identified as blocks along the Kill Chain, indicating mitigation measures and their efficacy in stopping or reducing the impact of a Threat Event.
Highlighted Paths
The Citadel highlights the most probable attack path using a Markov Decision Tree algorithm, predicting the likely sequence of Threat Events based on risk pathways.
Correlated Loss Events
Correlated Loss Events are identified and segregated by Primary and Secondary loss categories, aligned with the FAIR MAM (Factor Analysis of Information Risk Materiality Assessment Model ) framework to assess financial impact and risk exposure.
Loss event quantification
Citadel's AI-powered probabilistic engine analyses threat pathways to forecast attack probability and financialexposure, evaluating control efficacy and mitigation strategies to deliver actuarially sound cyber insurance insights. For each Loss Event Category, the tool delivers actionable intelligenceby synthesizing control efficacy, industry benchmarks, and actuarial data:
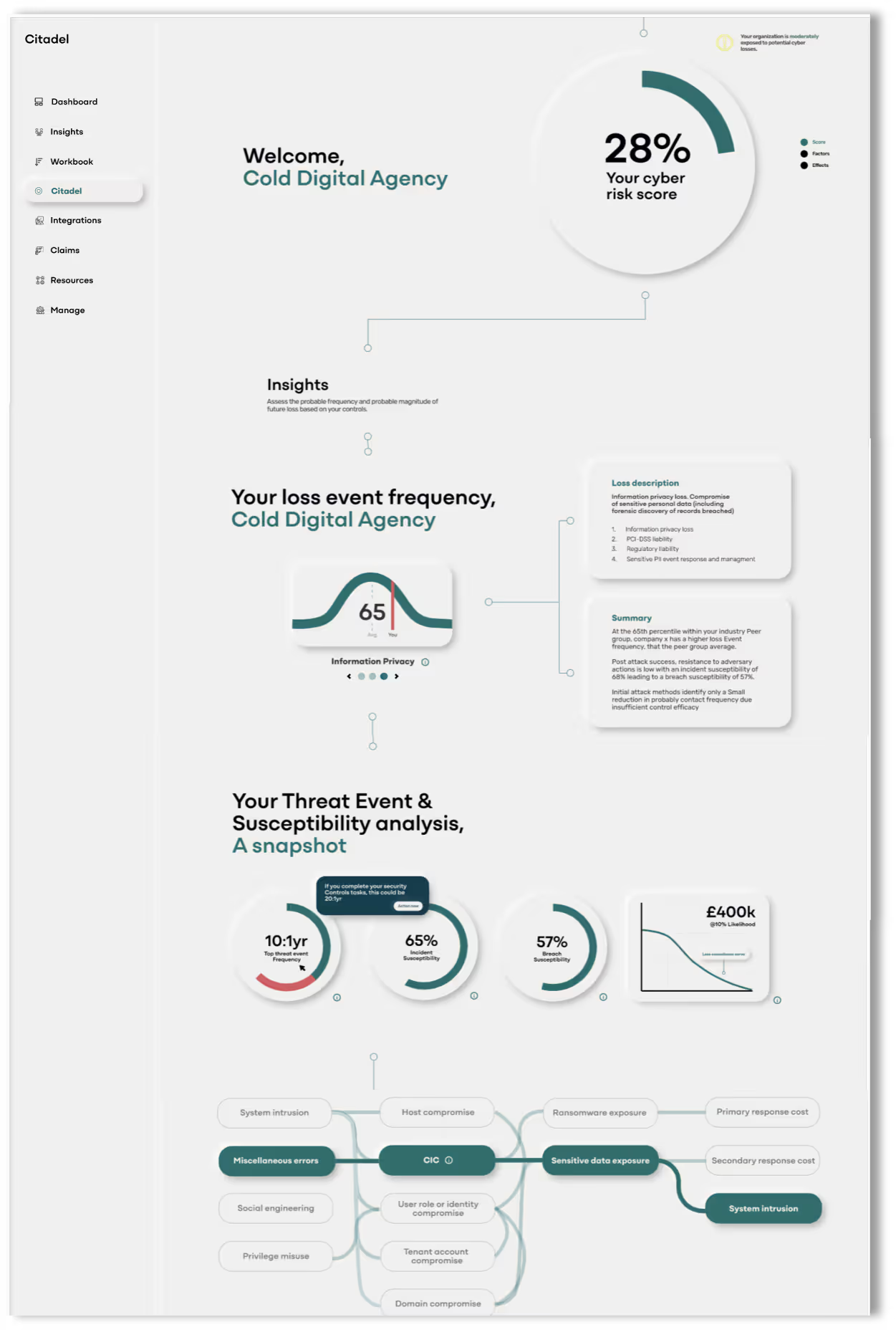
Peer-Group Benchmarking
Compares an organization’s risk posture against industry peers using normal distribution modelling. Identifies a percentile position per loss class.
Expected Event Frequency
In the context of the Selected Loss Class (e.g Information Privacy Loss) calculates contact frequency (initial threat attempts) with adjustments for avoidance control efficacy (how well defences prevent access)
System Susceptibility
In the event of a given “Initial Threat Event”, this measures Resistance Strength to both “Compromise” & “Breach”, used to determine the system susceptibility or inherent vulnerability
Actuarial-Grade Loss Modelling
Combines peer-group performance data, historical attack patterns, control efficacy and compromise and breach resistance strength to determine a Loss Exceedance Curve to predict loss magnitude at a given frequency
Loss Class Pathways
In the context of the Selected Loss Class (e.g Information Privacy Loss) calculates most probable Initial Threat Attempt, Correlating with the Susceptibility Impacts (Compromise & Breach Types)
Your Controls Exist - But Are They Actually Working? Citadel. Beyond Control Presence to ControlPerformance.
We gobeyond simply checking if controls exist to measuring how well they perform - analysing configuration accuracy, threat coverage, and prevention capabilities to calculate a definitive Efficacy Score.
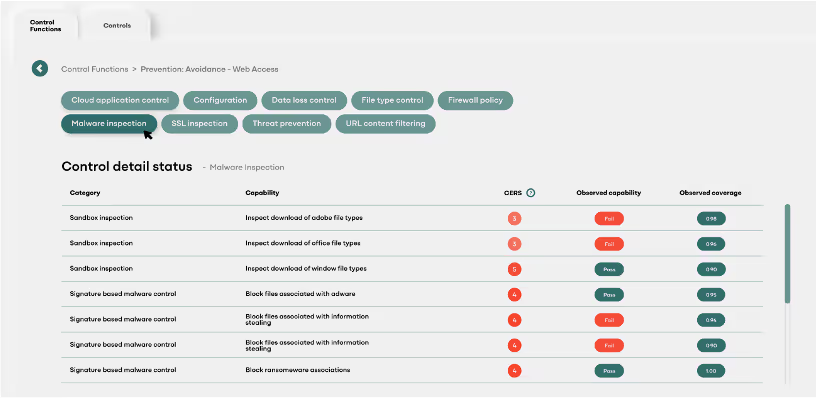
Contact Exposure Reduction Score
Cyber Logica's Contact Exposure Reduction Score (CERS) measures how effectively a control reduces adversarial contact frequency.
Capability Evaluation
Detection & prevention effectiveness against known TTPs
Coverage Analysis
Protected assets/user coverage ratio
Configuration Assessment
Alignment with security best practices
Simple cloud native integration of customer security controls for efficacy testing.
Cloud-Native API Integration for Avoidance Controls
Dynamic Data Ingestion:
• Securitypolicies (e.g., WAF rulesets)
• Featuredeployment states (e.g., enabled/disabled protections)
•Coveragemetrics (e.g., % of protected endpoints)
Automated Control Validation
Direct API integration with cloud-native security controls (e.g., CSPM, SWG, CASB) to assess real-time configuration status



AI-powered cyber risk prediction to assess threat, test defences & optimise insurance outcomes.
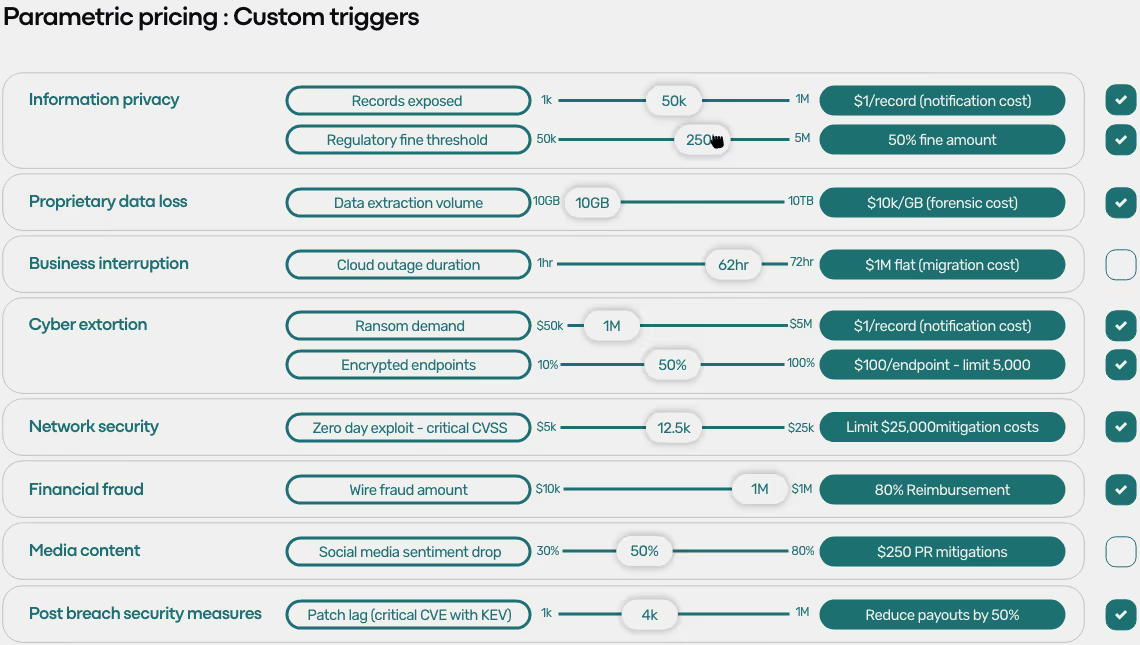
The power of parametric policies



The citadel approach
Citadel revolutionizes cyber insurance underwriting by combining real-time security performance data with AI-driven threat modelling to deliver dynamic, accurate pricing. Our methodology integrates five core elements:
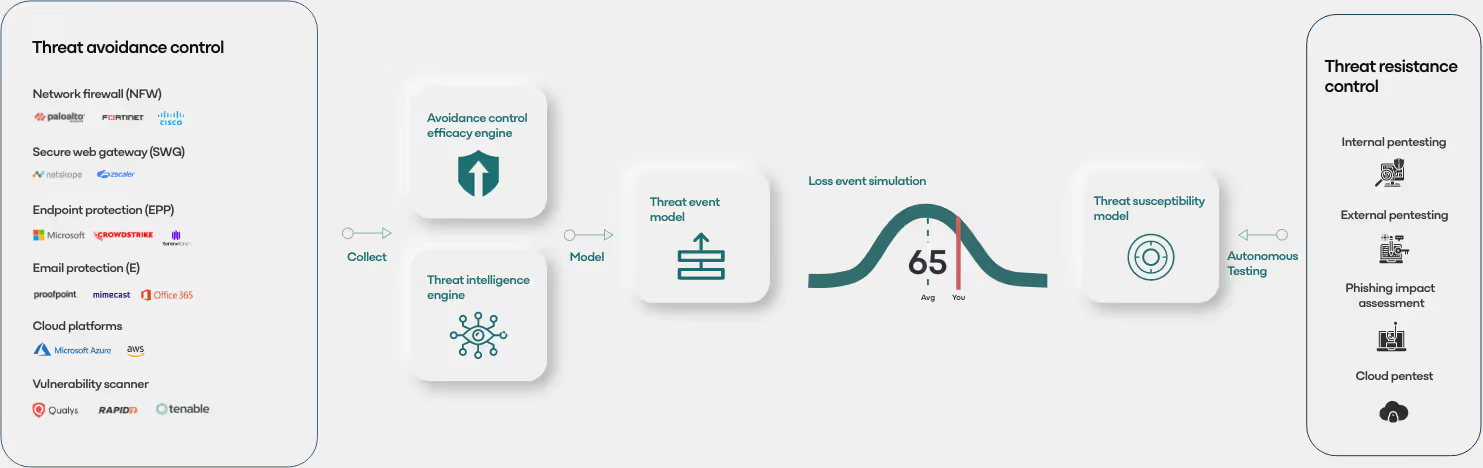
Threat Avoidance Control Ingestion
Cloud native API integrationAutomated collection of control configuration data across the security stack.
Interrogates control coverage, feature capability, and configuration state.
Control Performance Auditing
Continuously measures the operational effectiveness of security controls (e.g., configuration correctness, detection capability).
Generates an Efficacy Score for each control function, moving beyond "checkbox compliance" to proven risk reduction.
Adversary Exposure Analysis
Leverages threat intelligence to identify industry-specific attack patterns and likely adversaries.
Quantifies expected contact frequency based on the organization’s digital footprint, sector, and attacker TTPs.
AI-Powered Probabilistic Threat Chaining
Models multi-step attack pathways using graph-based AI to simulate how breaches propagate.
Predicts loss event likelihood by chaining vulnerabilities, control gaps, and adversary behaviours.
Autonomous Resistance Validation
Deploys AI-driven pentesting to stress-test defenses against realistic attack sequences.
Measures compromise resistance strength (e.g., mean time to detection, containment effectiveness).
Outcome
A closed-loop cyber risk ecosystem where:
Insurers gain granular risk visibility and reduced underwriting uncertainty.
Policyholders benefit from fair premiums tied to actual security posture.
Brokers access data to negotiate optimal coverage.



“Pioneer a future where cyber insurance isn’t a backup plan… it’s an AI-powered frontline defense.”



“Our mission is to redefine cyber insurance by leveraging cutting-edge AI to shift from reactive protection to proactive defense. We empower SMEs and enterprises worldwide with real-time underwriting, seamlessly integrating with global compliance standards and cloud ecosystems. By transforming cyber insurance into a frontline risk defense solution, we aim to set the industry benchmark—driving innovation through scalable solutions and disruptive partnerships, including Cloud Marketplaces, to make advanced cyber risk mitigation accessible to all.”



Based across London, UK and Ontario, Canada, we are a team of cybersecurity and risk management experts, founded by seasoned professionals with deep experience in delivering high-stakes cyber services to governments and global enterprises. Our background spans security operations, incident response, and proactive risk mitigation - giving us unique insight into the evolving threats businesses face today.
Driven by this expertise, we’re redefining cyber insurance. Unlike traditional models focused on post-breach recovery, we combine AI-powered underwriting with real-time risk prevention, turning insurance into an active layer of defense. Our platform bridges the gap between compliance, cloud ecosystems, and actionable security, ensuring businesses aren’t just insured, but resilient.




